1. What is a user?
In Linux user is one who uses the system. There can be at least one or more than one users in Linux at a time.
2. How many types of users are available in Linux?
There are 5 types of users available in Linux.
(i) System user (Admin user who control the whole system nothing but root user).
(ii) Normal user (Created by the Superuser. In RHEL - 7 the user IDs from 1000 - 60000).
(iii) System user (Created when application or software is installed and maintained system daemons).
(In RHEL - 7 the System users are (i) Static system user id's from 1 - 200 and (ii) Dynamic system user ids from 201 - 999).
(iv) Network user (Nothing but remote user, ie., who is login to the system through a network created in Windows Active Directory or in Linux LDAP or NIS).
(v) Sudo users (The normal users who are having admin or Super user privileges)
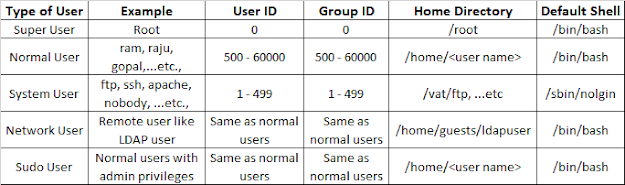
The types of users in Linux and their attributes:
| Type of User | Example | User ID | Group ID | Home Directory | Default Shell |
| Super User | Root | 0 | 0 | /root | /bin/bash |
| Normal User | ram, raju, gopal, ...etc., | 500 - 60000 | 500 - 60000 | /home/<user name> | /bin/bash |
| System User | ftp, ssh, apache, nobody, ...etc., | 1-499 | 1-499 | /vat/ftp, ...etc | /sbin/nolgin |
| Network User | Remote user like LDAP user | Same as normal users | Same as normal users | /home/guests/ldapuser | /bin/bash |
| Sudo User | Normal users with admin privileges | Same as normal users | Same as normal users | /home/<user name> | /bin/bash |
3. What is user management?
User management means managing user. ie., Creating the users, deleting the users, and modifying the users.
4. What are the important points related to users?
● Users and groups are used to control access to files and resources.
● Users can login to the system by supplying username and passwords to the system.
● Every file on the system is owned by a user and associated with a group.
● Every process has an owner and group affiliation.
● Every user in the system is assigned a unique user id (uid) and group id (gid).
● Usernames and user id are stored in /etc/passwd file.
● User's passwords are stored in /etc/shadow file in an encrypted form.
● Users are assigned a home directory and a shell to work with the O/S.
● Users cannot read, write, and execute each other's files without permission.
● Whenever a user is created a mailbox is created automatically in/var/spool/mail location.
● And some user environmental files like .bash_logout, .bash_profile, .bashrc , ...etc., are also copied from /etc/skell to his/her home directory (/home/<username>).
5 . What are fields available in /etc/passwd file?
<username> : x : <uid> : <gid> : <comment> : <user's home directory> : <login shell> (where 'x' means link to password file ie., /etc/shadow file)
6 . What are fields available in /etc/shadow file?
username : password : last changed : min. days : max. days : warn days : inactive days : expiry days : reserved for future
7. What are the files that are related to user management?
● /etc/passwd -----> Stores user's information like username, uid, home directory and shell ...etc.,
● /etc/shadow ----> Stores user's password in encrypted form and other information.
● /etc/group ------> Stores group's information like group name, gid and other information.
● /etc/gshadow ---> Stores group's password in encrypted form.
● /etc/passwd- ---> Stores the /etc/passwd file backup copy.
● /etc/shadow- ---> Stores the /etc/shadow file backup copy.
● /etc/default/useradd ----> Whenever the user created user's default settings taken from this file.
● /etc/login.defs ----> user's login defaults settings information taken from this file.
● /etc/skell ------> Stores user's all environmental variables files and these are copied from this directory to user's home directory.
8. In how many ways can we create the users?(i) # useradd - <options><username> (ii) # adduser - <options><username> (iii) # newusers <file name> (In this file we must enter the user details same as /etc/passwd file)9. What is the syntax ofuseradd command with full options?
# useradd -u <uid> -g <gid> -G <secondary group> -c <comment> -d <home directory> -s <shell><username>Example :
# useradd -u 600 -g 600 -G java -c "oracle user" -d /home/raju -s /bin/bash/ raju10. What is the syntax of adduser command with full options?
# adduser -u <uid> -g <gid> -G <secondary group> -c <comment> -d <home directory> -s <shell><username> Example: # adduser -u 700 -g 700 -G linux -c "oracle user" -d /home/ram -s /bin/bash ram11. What is the syntax of newuser command?
# newusers <file name> (This command will create multiple users at a time) * First we should a file and enter user's data as fields same as the fields of /etc/passwd file for how many users do you want to create and mention that file as an argument for newusers command. * When we execute this command new users will be created but their environmental files like .bash_logout, .bash_profile, .bashrc and .bash_history files will not be copied from /etc/skell directory. So, we have to copied manually from/etc/skell directory.12. What is the syntax of userdel command with full options?
## userdel <options><username> * The options are, -f -----> forcefully delete the user even through the user is login. The user's home directory, mail and message directories are also deleted. -r -----> recursively means files in the user's home directory will be deleted and his home directory also deleted but the other files belong to that user should be deleted manually.
13. How to check whether is already created or not?
We can check in different ways.(i) # id <user name> (It shows the user id group id and user name if that is already created) (ii) # cat /etc/passwd |grep <user name> (It shows the user's details if that user is already created)14. How to verify or check the integrity of the password file?
# pwck <options> /etc/passwd or # pwck <options> /etc/shadow * The options are, -q ------> quiet -r ------> read only -s -----> sort the contents by uidin /etc/passwd and /etc/shadow files.15. How to verify or check the integrity of the group file?
# grpck <options> /etc/group or # grpck <options> /etc/gshadow * The options are,16. What is syntax of the usermod command with full options?
-r -----> read only -s -----> sort the contents by gidin /etc/group and /etc/gshadow files.
# usermod <options><username> * The options are, -L -----> lock the password -U -----> unlock the password -o ----->creates duplicate user (modify the user's id as same as other user's id) -u ----->modify user id -g -----> modify group id -G -----> modify or add the secondary group -c -----> modify comment -d -----> modify home directory -s -----> modify user's login shell -l -----> modify user's login name -md ----> modify the users home directory and the old home directory also rename17. How to create the duplicate root user?
# useradd -o -u 0 -g root <username>18. How to recover if the user deleted by mistake?
# pwunconv ( It creates the users according /etc/passwd file and deletes the /etc/shadow file)19.What are the uses of .bash_logout, .bash_profile and .bashrc files?
.bash_logout : This is a user's logout ending program file. It will execute first whenever the user is logout.
.bash_profile : This is user's login startup program file. It will execute first whenever the user is login. It consists of the user's environmental variables.
.bashrc : This file is used to create the user's custom commands and to specify the umask values for that user's only.
20. What is a group?
The collection of users is called a group. There are two types of groups.
Primary group: It will be created automatically whenever the user is created. User belongs to on group is called primary group.
Secondary group: It will not create automatically. The admin user should be created manually, and users belongs to more than one group is called secondary group. A user can be assigned to max. 16 groups. ie., 1 primary group and 15 secondary groups.
21. What is the command to check the user belongs to how many groups?# groups <username>22. What is the syntax to create the group?
# groupadd <options><group name> The options are, -f -----> add the group forcefully -g -----> group id no. -o ----->non-unique (duplicate group id) -p -----> group password -r -----> system group -R -----> root group23. What is the syntax to modify the group?
# groupmod <options><group name> The options are, -g ------> group id -n ------> new name for existing one, ie., rename the group -o ------> non-unique (duplicate group id) -p ------> group passwd -R ------>root group24. What is syntax to delete the group?
# groupdel <group name> (to delete the group without options) # groupdel -R <group name> (to delete the group and apply changes to the root directory)25. How to assign the password to the group?
# gpasswd <group name> (to assign a password to the group without any options) # gpasswd <options><group name> The options are, -a ------>add users to the group -d ------> delete the user from the group -r ------> remove the group password -R ------> restrict to access that group -A ------> set the list of Administrative users -M ------> set the list of group members26. How to check the integrity or consistency of the group?
# grpck (it will check the integrity or consistency in /etc/gpasswd and /etc/gshadow files)27. How to restore /etc/gshadow file if deleted by mistake?
# grpconv (it creates the /etc/gshadow file from /etc/group file)28. How to change the password aging policies?
we can change the password policies in 2 ways.
(i) First open the /etc/login.defs file and modify the current values.
Example:# vim /etc/login.defs min - 0 -----> means the user can change the password to any no. of times. min - 2 -----> means the user can change the password within 2 days. ie., he can change the password after 2 days. max - 5 -----> means the user should change the password before or after 5 days. Otherwise, the password will be expired after 5 days. inactive - 2 -----> means after password expiry date the grace period another 2 days will be given to change the password. warning - 7 -----> means a warning will be given to the user about the password expiry 7 days before expiry date.(ii) second by executing the
# chage command.Example:
# chage <options><user name> The options are, -d -----> last day -E -----> expiry date -I -----> inactive days -l -----> list all the policies -m -----> min. days -M -----> max. days -w -----> warning daysNote : Whenever we change the password aging policy using # chage command, the information is will be modified in /etc/shadow file.
29. How add 45 days to the current system date?
# date -d "+ 45 days"33. How to assign the password to normal user by him whenever first login to the system Whenever the user is created and that user is trying to login to the system, it will ask the password. If the root user is not assign the password to that user, then that normal user can assign the password by his own using the following commands.
# useradd <user name> (to create the user) # passwd -S <user name> (to see the status of the password of that user. if root user is not assigned the password then the password status islocked) # passwd -d <user name> (then delete the password for that user) # chage -d 0 <user name> (it will change the password age policy) # su - <user name> (Try to switch to that user then it will display the following message) Newpassword : (type new password for that user) Retype password : (retype the password again)
34. How many types of the files are there?
There are 7 types of files.
1. - -----> regular file
2. d -----> directory
3. c -----> character device file (Ex. console file, open and close terminals, ...etc.,)
4. b -----> block device file (Ex. device blocks like hard disks, CD/DVD disks)
5. s -----> socket file (programmers will deal this file)
6. p -----> pipe file (programmers will deal this file)
7. l -----> linked file (nothing but short cut file)
35. What are permission types available in Linux and their numeric representations?| Permission | --- | r | --- | 4 |
|---|---|---|---|---|
| read | ----- | r | ----- | 4 |
| write | ----- | r | ----- | 4 |
| execute | ----- | r | ----- | 4 |
| Permissions | File | Directory |
|---|---|---|
| r | Read a file Ex. # cat <file name> | Read a directory contents Ex. ls /dir |
| w | Create, delete or modify the file contents | Create, delete or modify the files in a directory |
| x | Not required for file. It is required only for scripting files | Go to inside the directory Ex. # cd /dir |
# chmod <options><file name or directory name> (to change the owner or permissions of the file or directory) The options are, -c -----> changes -f -----> silent (forcefully) -v -----> verbose -R -----> recursive (including sub directories and files)To change the permissions the syntax is,
|
#chmod |
<who> |
<what> |
<which> |
<file name or directory> |
|
|
user (u) |
add (+) |
read (4) or (r) |
" " |
||
|
group(g) |
remove(-) |
write (2) or (w) |
" " |
||
|
other (o) |
equal (=) |
execute (1) or (x) |
" " |
# chown <options><file name or directory> (to change the ownership of the file or directory) The options are, -c -----> changes -f -----> silent (forcefully) -v -----> verbose -h -----> no difference -R -----> recursive (including sub directories and files) -H -----> symbolic link to a directory (command line argument) -L -----> symbolic link to a directory (all) -p -----> do not traverse # chown <username> : <group name> <filename or directory name> (to change owner and group ownership of the file or directory)38. What is syntax of chgrp command with full options?
# chgrp <options><file name or directory> (to change group ownership of the file directory) The options are, -c -----> changes -f -----> silent (forcefully) -v -----> verbose -h -----> no difference -R -----> recursive (including sub directories and files) -H -----> symbolic link to a directory -L -----> do not traverse-p -----> do not traverse39. What are the default permissions of a file and directory?
The default permissions of a file = 6 6 6
The default permissions of a directory = 7 7 7
40. What is umask in linux?
The user file-creation mode mask (umask) is used to determine the file permissions for newly created files or directories. It can be used to control the default file or directory permissions for new files. It is a four-digit octal number. The umask value for normal user is 0002 and the umask value for root user is 0022.
So, the effected file permissions for normal users = 6 6 6 - 0 0 2 = 6 6 4. The effected directory permissions for normal users = 7 7 7 - 0 0 2 = 7 7 5. The effected file permissions for root user = 6 6 6 - 0 2 2 = 6 4 4
The effected directory permissions for root user = 7 7 7 - 0 2 2 = 7 5 5# umask <value> (to change the umask value temporarily) # vim /etc/bashrc (open this file and change the umask value to effect the whole system) # source /etc/bashrc (to updated the source file) # vim .bashrc (open this file in user's home directory and at last type as follows) umask <value>(save and exit the file) # source .bashrc or logout and login again (to the system to effect that umask value)* If the/etc/login.defs file is corrupted then new users will be added and can be assigned the passwords, but users cannot login.
* If the /etc/login.defs file is deleted then new users cannot be added.
41. How change the permissions using numeric representation?
The values for read = 4, write = 2, execute = 1 and null = 0. The total value = 4 + 2 + 1 = 7 # chmod <no.><no.><no.><file name or directory name>
Example :# chmod 774 file1 (to give read, write and execute to owner and read, write and execute to group and read permission to others) # chmod 660 file2 (to give read and write to owner and read and write to group and null (0) permission to others)
42. Explain about set uid (suid)?
If we plan to allow all the users to execute the root users command then we go for set uid (suid). It can be applied for user level and is applicable for files only.# chmod u+s <file name> (to set the suid on that file) # chmod u-s <file name> (to remove the suid from that file) # ls -l (if 'x' is replaced with 's' in owner's level permissions that means suid is applied on that file) - r w s r w x r w x <file name> (here 's' is called set uid or suid)Example :
# chmod u+s /usr/sbin/init 6 (then any user can restart the system using this command #init 6) # chmod u+s /sbin/fdisk (then any user can run the fdisk command) # strings <command name> (to read the binary language of the command ie., the string command converts the binary language into human readable language) # strings mkfs (to read the mkfs command's binary language into human readable language)* Normally set uid (suid) permission will be given on scripting files only.
43. Explain about set gid (sgid)?
If we plan to allow all the users of one group to get the group ownership permissions then we go for set gid (sgid). It can be applied for group level and is applicable on directories only.
Example:# chmod g+s <directory name> (to set the sgid on that directory) # chmod g-s <directory name> (to remove the sgid from that directory)
44. Explain about sticky bit?
It protects the data from other users when all the users having full permissions on one directory. It can be applied on others level and applicable for directories only.
Example :# chmod o+t <directory name> (to set the sticky bit permission on that directory) # ls -ld <directory name> r w x r w x r w t <directory name> (where 't' is called the sticky bit)45. What are the uses of passwd and shadow files?
Passwd file : (i) When we create the user one entry is updated in password and shadow files.
(ii) It represents and tell about that user login name , uid, gid, default home directory of the use and default shell.
(iii) So, using this file we can easily get users information.
Shadow file : (i) This file tells about the login id, user's encrypted password, password when last changed, min. days the password valid, max. days valid, warning days, inactive days and expiry days.
(ii) If shadow file is missed or deleted we can recover those entries of shadow file using password file.
(iii) We can change the users encrypted passwords with the permissions of the higher authorities in case of emergency.
46. What is the use of group?
(i) In an organization the whole work is divided into departments for easy maintenance and easy administration.
(ii) For each department is also represented as group and that group having so many users to do different works.
(iii) So, if we create one group and assign that group to all the users in that department, then we can easily identify which user belongs to which group.
(iv) We can share files, directories and execute some programs to that group and also give permissions to that group. So, each user of that group can easily share those directories and also can easily access, execute or even write in those shared files and directories.
47. Can we login to the user without password?
Yes, we can login.
48. How to recover the root password if missed or deleted?
RHEL - 7, 8:
(i) Restart the system.
(ii) Using arrow keys select 1st line and press 'e' to edit.
(iii) Go to Linux 16 line press End key or Ctrl + e to go to the end of the line and give one space.
(iv) Then type asrd.break console=tty1 selinux=0
(v) Then press Ctrl + x to start the computer in single user mode.
(vi) After starting we get swith_root :/# prompt appears and then type as follows (vii) # mount -o remount, rw /sysroot and press Enter and then type as follows. (viii) # chroot /sysroot press Enter.
(ix) Then sh - 4.2 # prompt appears and type as
(x) sh - 4.2 #passwd root
New password : XXXXXX Retype password : XXXXXX
(xi) sh - 4.2 # exit
(xii) switch-root :/# exit
(xiii) Then the system starts and the desktop appears.
49. How to restrict the users from login?
(i) By removing (deleting) the user we can restrict the user from login.
(ii) Put the user's hostnames as entries in /etc/hosts.deny file (applying TCP wrappers). (iii) #passwd -l <user name> (by locking his password we can restrict the users).
50. How to put never expiry to a user?
# passwd -x -1 <user login name>51. Which one is the default sticky bit directory?
/tmp is the default sticky bit directory.
52. What is the purpose of the profiles?
(i) Profile is a file to enter some settings about users working environment. ie., we can set user home directory, login shell, path, ...etc.,
Profiles are two types.
(a) Global profile
(b) Local profile
Global profile:
(1) Only root user can set and applicable to all the users.
(2) Only global parameters can enter in this profile.
(3) The location of the global profile is /etc/bashrc
Local profile:
(1) Every user has his/her own profile.
(2) The settings entered in this profile are only for that user.
(3) The location of the profile is .bash_profile (hidden file) in that particular user's home directory.
53. Can we mount/unmount the O/S file system?
No, we cannot mount or unmount the O/S file system.
54. How to find the users who are login and how to kill them?
# fuser -cu (to see who are login) #fuser -ck <user login name> (to kill the specified user)55. what is Access Control List (ACL)?
Define more access rights nothing but permissions to files and directories. Using Access Control list we assign the permissions to some particular users to access the files and directories.
ACL can cab be applied on ACL enabled partition that means you need to enable ACL while mounting the partition.
56. How to implement ACLs?
● Create a partition and format it with ext4 file system.
● Mount the file system with ACL.
● Apply ACL on it.
Create a partition using# fdisk command. Format the above partition with ext4 file system using # mkfs.ext4 <partition name> command. Create the mount point using # mkdir /<mount point> command. Mount that file system on the mount point using # mount -o acl <partition name><mount point> command. Mount the partition permanently using # vim /etc/fstab (open this file and make an entry as below) <partition name><mount point><file system type> defaults, acl 0 0 Save and exit this file.If the partition is already mounted then just add acl after defaults in /etc/fstab file and execute the below command
# mount -o remount <partition name>
57. How to check the ACL permissions?
# getfacl <options><file or directory name>58. How to assign ACL permissions?The options are, -d -----> Display the default ACLs. -R -----> Recurses into subdirectories.
# setfacl <options><argument> : <username>: <permissions><file or directory name> The options are, -m -----> Modifies an ACL. -x -----> Removes an ACL. -b -----> Remove all the ACL permissions on that directory. -R -----> Recursive into subdirectories. The arguments are, u -----> user g -----> group o -----> other59. What is the syntax to assign read and write permissions to particular user, group and other?
# setfacl -m u : <user name> : <permissions><file or directory> # setfacl -m g : <user name> : <permissions><file or directory> # setfacl -m o : <user name> : <permissions><file or directory>60. What is the syntax to assign read and write permissions to particular user, group and other at a time?
# setfacl -m u : <username> : <permissions>, g : <username> : <permissions>, o : <username> : <permissions><file or directory>Useful commands:
# setfacl -x u : <username><file or directory name> (to remove the ACL permissions from the user) # setfacl -x g : <username><file or directory name> (to remove the ACL permissions from the group) # setfacl -x o : <username><file or directory name> (to remove the ACL permissions from the other) # setfacl -b <file or directory> (to remove all the ACL permissions on that file directory)
61. How will you lock a user, if he enters wrong password 3 times?
pam_tally.so module maintains a count of attempted accesses, can reset count on success, can deny access if too many attempts fail. Edit /etc/pam.d/system-auth file, enter:(i) # vi /etc/pam.d/system-authModify as follows: auth required pam_tally.so no_magic_root account required pam_tally.so deny=3 no_magic_root lock_time=180
Where,
▪ deny=3 : Deny access if tally for this user exceeds 3 times.
▪ lock_time=180 : Always deny for 180 seconds after failed attempt. There is alsounlock_time=n option. It allow access after n seconds after failed attempt. If this option is used the user will be locked out for the specified amount of time after he exceeded his maximum allowed attempts. Otherwise, the account is locked until the lock is removed by a manual intervention of the system administrator.
▪ magic_root : If the module is invoked by a user with uid=0 the counter is not incremented. The sys-admin should use this for user launched services, like su, otherwise this argument should be omitted.
▪ no_magic_root : Avoid root account locking, if the module is invoked by a user with uid=0 Save and close the file.
62. How to see the no. of failed logins of the users?# faillog -u <user name> (to see the specified users failed login attempts) # faillog -a (to see failed login attempts of all users) # faillog -M <Max. no> -u <user name> (to set Max. login failed attempts to that user) # faillog -M 5 -u raju (to set Max. login failed attempts to 5 for user raju)63. What is disk quotas and how to enable them?
By configuring the disk quotas we can restrict the user to use unlimited space on the file system and also to restrict the unlimited files in the file system. We can configure the disk quotas in ways. They are,
(i) user quotas
(ii) group quotas
Steps to enable:
First check whether the quota package is installed or not by
# rpm -qa |grep quota command. If quota package is not Installed then install the quota package by # yum install quota* -y command. # quotaon (to enable the quota) # quotaoff (to disable the quota) # edquota (to edit or modify the quota) # repquota (to display or report the present quota) # quotacheck (to create a quota database) * quotas cab be applied on file systems only.64. How to enable the user quota on a file system? (i) Open the /etc/fstab file by
# vim /etc/fstabcommand and goto the mount point entry line and type as, /dev/sdb1 /mnt/prod ext4 defaults, usrquota 0 0 (save and exit this file)(ii) Update the quota on mount point by # mount -o remount, usrquota <mount point> command. (iii) Create the user quota database by # quotacheck -cu <mount point> command (where -c means created the quota database and -u means user quota). (iv) Check whether the quota is applied or not by # mount command. (v) Enable the quota by # quotaon <mount point> command. (vi) Apply the user quota for a user by # edquota -u <username><mount point> command.
|
File system |
blocks |
soft |
hard |
inodes |
soft |
hard |
|
/dev/sdb1 |
0 |
0 |
0 |
0 |
0 |
0 |
blocks -----> No. of blocks used (already)
soft -----> Warning limit
hard -----> Maximum limit
0 -----> Unlimited usage
inodes -----> No. of files created (already)
* If soft=10 and hard=15 means after crossing the soft limit a warning message will be displayed and if hard limit is also crosses then it won't allow to create the files for that user.
(save and exit the above quota editor)
65. How to enable the quota on block level?
(i) Apply the user quota for a user by# edquota -eu <username><mount point>command
|
File system |
blocks |
soft |
hard |
inodes |
soft |
hard |
grace period |
|
/dev/sdb1 |
0 |
5000 |
10000 |
0 |
0 |
0 |
6 days |
(save and exit the quota editor)
soft=5000 -----> means if it reaches upto 5MB, there is no warnings. If it exceeds ie., from 5MB - 10MB there will be warnings messages displayed, but the files will be created.
hard=10000 ---> If it reached to 10MB, then it will not allow to create the files. The grace period by default is 7 days. So, we can change the grace period by #edquota -t command, here we can change the default 7 days grace period to our required days of grace period. Grace period means, if the user not created any files within the grace period days the soft limit becomes as hard limit. ie., soft and hard limits are equal.
# edquota -p <user name 1><user name 2> (to apply user name 1 quotas to user name 2, ie., no need to edit the quota editor for user name 2)66. How to enable the group quota?
(i) Open the /etc/fstab file by
# vim /etc/fstab command and goto the mount point entry line and type as, /dev/sdb1 /mnt/prod ext4 defaults, grpquota 0 0 (save and exit this file)(ii) Update the quota on mount point by
# mount -o remount, usrquota, grpquota <mount point>command.(iii) Create the user quota database by
# quotacheck -cug <mount point> command (where -c means created the quota database, -u means user quota and -g means group quota ).(iv) Check whether the quota is applied or not by
# mount command.(v) Enable the quota by
# quotaon <mount point> command.(vi) Apply the user quota for a user by
# edquota -g <group name><mount point> command.File system blocks soft hard inodes soft hard
/dev/sdb1 0 0 0 0 0 0
blocks -----> No. of blocks used (already)
soft -----> Warning limit
hard -----> Maximum limit
0 -----> Unlimited usage
inodes -----> No. of files created (already)
* Here we can specify the block level quota or file level quotas.
* group quota can be applicable to all the users of that specified group.
(save and exit the above quota editor)
67. How to change the password for multiple users at a time?# chpasswd (to change multiple user's passwords) <username 1> : <password> <username 2> : <password> <username 3> : <password> <username 4> : <password> <username 5> : <password> (Ctrl + d -----> to save and exit)
* Then the above 5 user's passwords will be changed at a time. But here the passwords will not be encrypted while typing passwords. So, anybody can see the passwords. ie., there is no security.